This post will include basic introduction to metasploit & its working.
What is Metasploit ?
The Metasploit Project is an open-source computer security project which provides information about security vulnerabilities and aids in penetration testing and IDS signature development. Its most well-known sub-project is the Metasploit Framework, a tool for developing and executing exploit code against a remote target machine. Other important sub-projects include the Opcode Database, shellcode archive, and security research.
Basically Metasploit is tool which provides complete environment for hacking.
Metasploit is available in 3 versions
you can download metasploit from official website - www.metasploit.com
Working of Metasploit

Basically metasploit works on these 5 things
To take advantage of a vulnerability, you often need an exploit, a small and highly specialized computer program whose only reason of being is to take advantage of a specific vulnerability and to provide access to a computer system. Exploits often deliver a payload to the target system to grant the attacker access to the system.Here is a article on basic working of EXPLOITS
What is a payload?
A payload is the piece of software that lets you control a computer system after it’s been exploited. The payload is typically attached to and delivered by the exploit. Just imagine an exploit that carries the payload in its backpack when it breaks into the system and then leaves the backpack there.
Basically payload is the way you want to hack your target.Meterpreter is the most reliable payload & we will use it in most of the cases ahead
What is auxiliary?
Metasploit comes with 358 auxiliary.Basically auxiliary is used for information gathering before exploitation for ex if the machine is vulnerable to an attack or not . Here is video on email extractor auxiliary.
What are Nops & Encoders?
Metasploit comes with 8nops & 27 encoders these are used to bypass antiviruses/firewall via different techniques
So moving on to metasploit framework & some important commands
metasploit console is easy to understand if one uses his common sense
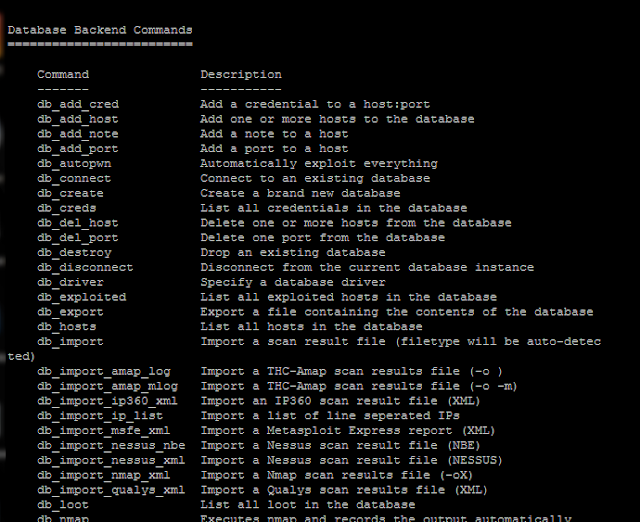
the help command does the trick.It shows all the commands available in metasploit.
We will move onto series of discussions & tutorial on metasploit later
Links worth spending time:
metasploit unleashed
Corelan
Dont forget to subscribe to our email updates
What is Metasploit ?
The Metasploit Project is an open-source computer security project which provides information about security vulnerabilities and aids in penetration testing and IDS signature development. Its most well-known sub-project is the Metasploit Framework, a tool for developing and executing exploit code against a remote target machine. Other important sub-projects include the Opcode Database, shellcode archive, and security research.
Basically Metasploit is tool which provides complete environment for hacking.
Metasploit is ran by rapid7 community & Metasploit is the biggest software which is written in rubyWhy metasploit is recommended ?
- metasploit is free n easy to use and one can develop his own exploits,payloads etc & use it with metasploit easily.
- It comes with over 690 exploits & which are updated on regular basis(0days also included).
- We can use diffrent plugins,external tools to improve the productivity of metasploit for example SET(social engineering toolkit), beEF, XSSF, Nexpose , NMAP, W3af etc(we will continue to it in next posts)
Metasploit is available in 3 versions
- Metasploit Pro - for pentester
- Metasploit Express- for IT security teams
- Metasploit Framework - Its an open source & avialable for download for free
you can download metasploit from official website - www.metasploit.com
Working of Metasploit

Basically metasploit works on these 5 things
What is an exploit -
- EXPLOIT
- PAYLOADS
- AUXILIARY
- NOPS & ENCODERS
To take advantage of a vulnerability, you often need an exploit, a small and highly specialized computer program whose only reason of being is to take advantage of a specific vulnerability and to provide access to a computer system. Exploits often deliver a payload to the target system to grant the attacker access to the system.Here is a article on basic working of EXPLOITS
What is a payload?
A payload is the piece of software that lets you control a computer system after it’s been exploited. The payload is typically attached to and delivered by the exploit. Just imagine an exploit that carries the payload in its backpack when it breaks into the system and then leaves the backpack there.
Basically payload is the way you want to hack your target.Meterpreter is the most reliable payload & we will use it in most of the cases ahead
What is auxiliary?
Metasploit comes with 358 auxiliary.Basically auxiliary is used for information gathering before exploitation for ex if the machine is vulnerable to an attack or not . Here is video on email extractor auxiliary.
What are Nops & Encoders?
Metasploit comes with 8nops & 27 encoders these are used to bypass antiviruses/firewall via different techniques
So moving on to metasploit framework & some important commands
metasploit console is easy to understand if one uses his common sense
the help command does the trick.It shows all the commands available in metasploit.

We will move onto series of discussions & tutorial on metasploit later
Links worth spending time:
metasploit unleashed
Corelan























